As IT is increasingly used in business, so is there an increase in the number of cyberattacks and the damage they cause.
Meanwhile, confidential information related to corporate business and the personal information of customers are being shifted to data-based management.
While such data management is convenient, as long as a computer is connected to the Internet, there is a risk of being attacked from the outside.
To protect against the theft of your confidential data, robust protection is essential.
Security has become one of the most important issues facing company managers.
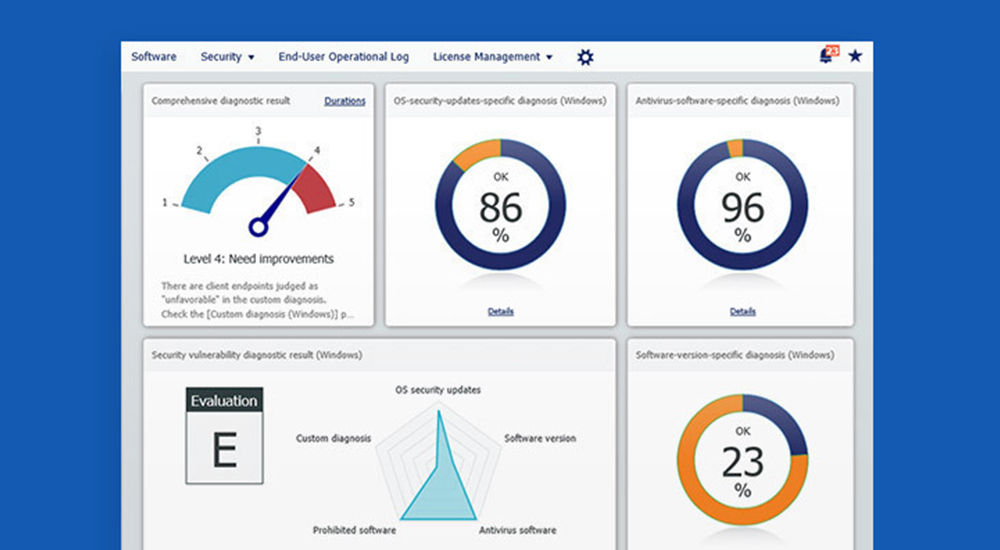
Do you have these issues?

We know we need better security, but we don't know where to start.

We want to strengthen security, but we don't have enough human resources.

We want security that suits hybrid work styles.

We want to know where our company's security is lacking.

We want to know about Zero Trust
Building efficient and consistently high-quality system infrastructures
One-stop provision of design, construction, introduction, and operation for systems
Intelligence cycle for building, operating and planning an ideal IT environment
Greatly reduce work load by fully outsourcing infrastructure, operation, and concept planning

One-stop solutions for security issues at overseas offices
Ideal for strengthening global security governance

Protect
Developing and implementing appropriate safeguards to ensure the delivery of critical services.
| ・ | Identity and Access Management (IAM) |
| ・ | Data loss prevention |
| ・ | Access control |
| ・ | Cloud security |
Detect
Development and implementation of appropriate actions to identify cybersecurity event occurrences.
| ・ | EDR(Endpoint Detection and Response)Threat detection |
| ・ | Intrusion detection systems |
Respond
Deployment and implementation of appropriate measures for detected cybersecurity incidents.
| ・ | SOC |
| ・ | Security Incident Management |
Recover
Recovery plan maintenance, as well as planning and implementation of appropriate actions to restore functions and services that have been compromised in cybersecurity incidents.
| ・ | Risk assessment |
| ・ | Penetration testing |
| ・ | Vulnerability testing |
Identify
Improve organizational understanding to better manage cybersecurity risks to systems, people, assets, data and capabilities.
| ・ | Risk assessment |
| ・ | Penetration testing |
| ・ | Vulnerability testing |
Training
Measures to improve the security literacy of employees to prevent vulnerabilities and accidents.
| ・ | Phishing email drills |
| ・ | e-learning |
| ・ | Security incident response training |
Why customers choose KDDI

All-in-one offerings
We provide end-to-end services for security ranging from infrastructure construction to operation to user support

Strengthened security governance
We enable you to strengthen your global security governance through cooperation between regions
Let KDDI guide you to Zero Trust solutions that support diversifying work styles.
Line up





Related White Papers
Steps to introducing zero trust for global companies

Key Points for Security Measures at Overseas Locations

Related Knowledge Articles



Related Case Study


What is the best solution for your problem?
Please consult a KDDI consultant.